In 2023, there were 6.42 million property crime incidents in the U.S. These property crime incidents, ranging from theft and vandalism to break-ins, highlight the critical importance of adequate perimeter security. The impact extends beyond the initial loss, as a single incident can lead to higher insurance premiums, reputational damage, and operational disruptions.
While some companies opt for a reactive approach to security, responding after an incident occurs, there are significant costs associated with this strategy. This article explores the pitfalls of a reactive approach and how a more proactive perimeter security strategy can safeguard your business.
Understanding Reactive Perimeter Security
Reactive perimeter security refers to measures that are taken following an incident. Typically, there is a “wait and see” mentality involved, which assumes that minimal security measures will deter criminals. Businesses that employ a reactive security approach often make assumptions that can prove costly, such as:
- Incidents are inevitable and cannot be prevented entirely
- Their location or industry makes them less likely targets
- The costs of proactive physical security outweigh the potential losses from security breaches
- Responding to incidents as they occur is sufficient to mitigate damages
Common examples of reactive security measures include:
- Installing security cameras, additional locks, or barriers after a break-in
- Hiring security personnel following a vandalism incident
- Repairing damaged fences or gates post-intrusion
While these actions are necessary, relying solely on a reactive approach leaves businesses vulnerable. Criminals are opportunistic — they strike when defenses are low, and the damage can be severe.
Direct Costs of Reactive Security
The direct risks of reactive security can be substantial, affecting a company’s bottom line and financial stability. Here are the most significant expenses that businesses face when relying on a reactive approach:
Property Damage and Loss
Security breaches often result in property damage and loss, which can be costly to repair or replace. Vandalism, forced entry, and external theft can lead to significant business expenses, including the repair of damaged assets and the replacement of stolen inventory. The losses can devastate companies or facilities that rely on high-value equipment or inventory.
Increased Insurance Premiums
Following a security incident, businesses may face higher insurance premiums due to the claims filed. Insurance providers assess risk based on an organization’s history of security breaches. A reactive perimeter security approach often leads to frequent security incidents, resulting in a perceived increase in risk. In some cases, businesses may struggle to obtain coverage due to their security track record, which leaves them vulnerable to future losses.
Incident Response Expenses
When a security breach occurs, businesses face immediate expenses related to incident response. These costs include:
- Labor costs for security personnel to investigate and secure the scene
- Private forensic investigation costs to gather evidence and identify the perpetrators
- Legal fees associated with pressing charges or dealing with legal consequences
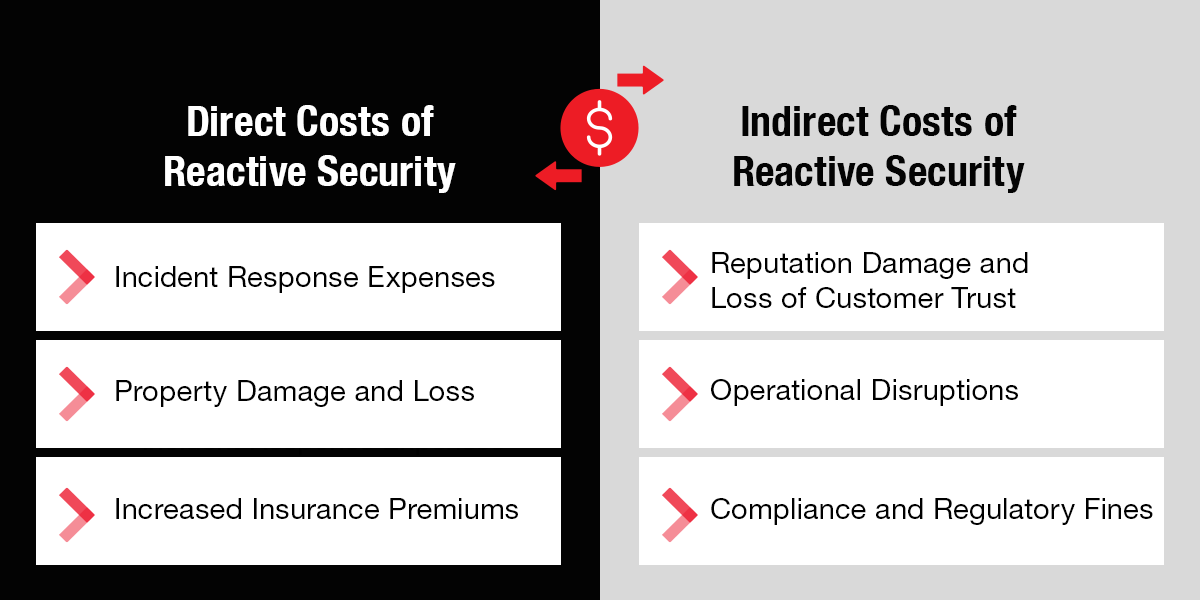
Indirect Costs of Reactive Security
Beyond the direct financial impact, a reactive security approach results in indirect costs that can have long-lasting effects on a company. These costs can be challenging to quantify, but they do significantly impact the bottom line.
Reputation Damage and Loss of Customer Trust
Security breaches can impact brand image and customer trust. Customers who learn about a security incident may lose confidence in the business’s ability to protect their personal information or assets. A damaged reputation can be difficult to repair, potentially leading to declining sales. Attracting new customers can also become challenging as they may be hesitant to engage with a business that has a history of security issues.
Operational Disruptions
Security breaches can lead to significant operational disruptions, impacting productivity and service delivery. When a breach occurs, businesses may need to temporarily shut down operations to investigate the incident and implement corrective measures. Security incidents can sometimes lead to more long-term disruptions, particularly if critical equipment or systems are damaged or compromised. These disruptions can impact supply chains, customer service, and efficiency.
Compliance and Regulatory Fines
For those operating in regulated industries, such as healthcare, finance, or energy, security breaches can result in significant compliance and regulatory fines. These sectors often have strict requirements for protecting sensitive information and assets, such as the PCI Security Standards Council (PCI SSC) DSS requirements. Failure to comply with these regulations, even if accidental due to a security breach, can lead to substantial penalties.
How a Proactive Perimeter Security Approach Can Control These Costs
With these costs in mind, companies should opt for a perimeter security strategy that anticipates would-be criminals and addresses the issues early. A proactive approach to perimeter security focuses on preventing security breaches before they occur, preventing the costly consequences of a more reactive strategy.
In addition, scheduling threat assessments of your business’s perimeter security posture helps you identify potential vulnerabilities. Security experts use the risk assessment results to recommend proactive measures to improve your security before criminals can exploit your system’s weaknesses.
Deterring Unauthorized Access
The main benefit of proactive security is deterring unauthorized access. Creating physical and psychological barriers allows facilities to discourage potential intruders from attempting to breach the perimeter. Opt for a comprehensive perimeter security plan including:
- Electric fencing: An electric fence is a visible and imposing barrier that sends a clear message about the property’s security level. If a would-be intruder tries to breach the perimeter, they receive a safe but memorable electric pulsed shock to deter them. The Electric Guard Dog™ Fence has pulsed electricity every 1.3 seconds, which makes it safe.
- Alarm-based lighting: Perimeter alarm-based security lights are a critical component of proactive physical security. When the electric fence alarm is triggered, the system detects any unauthorized activity along the perimeter. If there is unauthorized activity, the lighting system floods the area with light — deterring intruders and alerting security personnel to the potential threat.
- Access control systems: Access control ensures only authorized personnel can enter the premises. A unified access control system features credential readers, license plate recognition, motorized gate integration, and video intercoms — helping to reduce the risk of unauthorized access and potential security incidents.
These deterrents help companies proactively minimize the risk of a successful breach of their perimeter.
Choose AMAROK for Proactive, Multi-Layered Perimeter Security Solutions
The cost of reactive perimeter security can financially and operationally devastate a business. By understanding the risks associated with a reactive approach and embracing more proactive security measures, you can safeguard your organization from losses due to security breaches. Partner with AMAROK to implement a comprehensive and integrated perimeter security strategy with multi-layered solutions that proactively deter and detect potential threats.
Ensure the safety of your assets, people, and reputation — contact your local security expert today.






