Businesses across a wide range of industries have seen a steep increase in theft in recent years. The trucking industry alone experienced a 27% increase in cargo theft from 2023 to 2024, highlighting the need for more robust perimeter security.
Criminals target commercial sites that have clear vulnerabilities and predictable weaknesses. A multi-layered approach removes those weak points by making it more challenging to breach the perimeter. Each layer plays a role in stopping crime before it happens or detecting and delaying any crimes in progress.
To improve security with a layered approach, you need an integrated system that deters, detects, denies, delays, and defends against intruders.
How Layered Security Prevents Crime — the Five D’s of Physical Security
As physical security incidents among businesses continue to rise, it’s essential to adopt a unified approach that protects your assets, people, infrastructure, and reputation. A layered approach to perimeter security based on the five D’s ensures there are multiple barriers to stop intruders before they reach your critical assets.
Each layer in the five D’s of security builds on the other, providing a comprehensive approach to safeguarding your site and strengthening your facility’s defenses:
- Deter: Send the message that your site is well-protected with multi-layered deterrence measures like security lighting and imposing fences with warning signs. The goal is to make your property look like a risky target.
- Detect: Some criminals may still attempt to breach your perimeter despite these deterrents. In this case, it’s critical to have early detection solutions to ensure a rapid response, like video surveillance and alarms.
- Deny: You want to make it as challenging as possible for criminals to access your property. Restrict entry to authorized personnel only using reinforced gates, security fencing, and access control measures.
- Delay: With a multi-layered security plan, you can ensure that in the event of a perimeter breach, you can delay the intruder’s progress. Slow down criminals using solutions like building access restrictions to both prevent asset loss and give security personnel time to respond.
- Defend: The focus here is on security personnel actively intercepting and neutralizing an intrusion as well as collaborating with law enforcement. It’s imperative that your business has robust security protocols in place.
The Multi-Layered Perimeter Security Approach
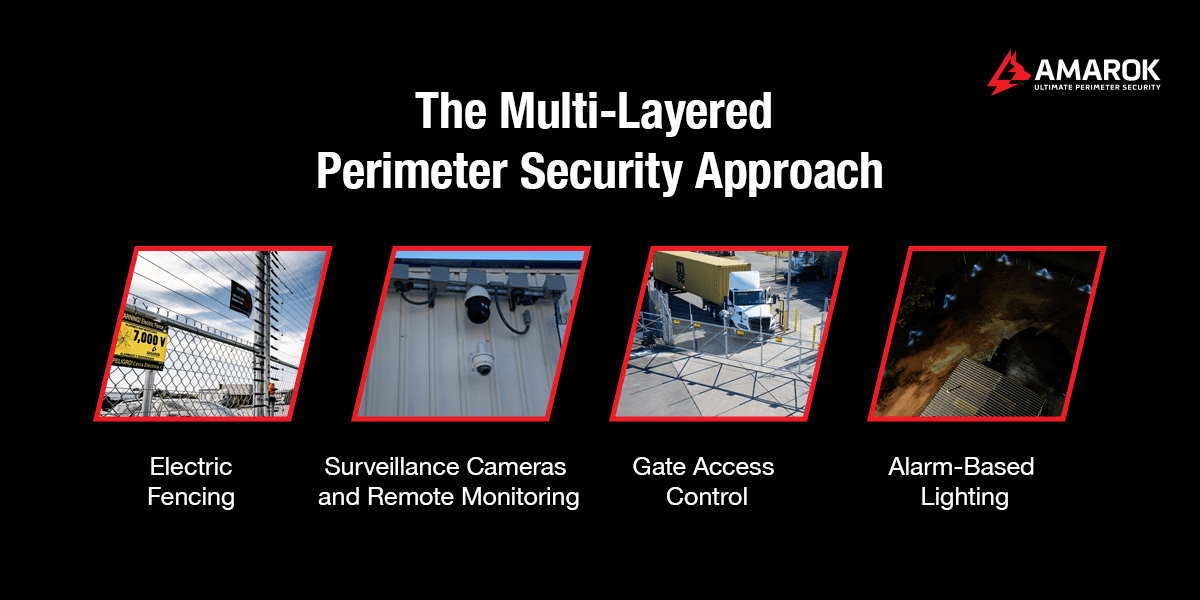
An effective layered approach to physical security starts with installing robust fencing — but it doesn’t stop there. Adopt multiple layers of protection to safeguard your business assets, protect your brand reputation, and achieve peace of mind.
The main components of a unified security strategy include:
1. Electric Fencing
An electric fence deters thieves by delivering a safe but memorable pulsed shock if there is an attempted breach. Electric fencing along with warning signs also act as a visual deterrent for would-be intruders, clearly showing that your commercial site is well-protected and not worth the risk.
Your electric fence is your first layer of defense, providing both an intimidating barrier and a shocking deterrent.
2. Surveillance Cameras With Remote Monitoring
High-definition video surveillance cameras provide visibility for key areas like gates, blind spots, and corners. Capture compelling evidence of criminal activity in real time, then review and share this footage with law enforcement to support your overall security response protocols.
With remote monitoring, there is always someone keeping an eye on your site, every day of the year. A mobile video monitoring solution offers around-the-clock surveillance for immediate threat verification and response.
A combination of surveillance cameras and real-time monitoring increases the odds of catching criminals in the act.
3. Gate Access Control
Deny entry to your site with robust access control measures, including at every entrance and exit. Gate Access Control ensures that only authorized personnel enter your property. With credential readers, audio and video intercoms, license plate recognition, and specialized gate locks, this layer adds accountability and control at all access points.
Access control is especially critical for industries with high vehicular traffic, like distribution centers and trucking companies.
4. Alarm-Based Lighting
Adding alarm-based lighting to your multi-layered security strategy helps deter intruders from attempting a breach. If the electric fence alarm is triggered, the lighting system is activated and floods the area with light. Zone fence lighting uses energy-efficient LEDs, which are customizable to target specific points along your perimeter.
Easily integrate alarm-based lighting with your electric fencing and other solutions like remote monitoring and surveillance cameras.
Consider Industry-Specific Compliance Requirements
Perimeter security measures must follow local laws and industry regulations. Check for restrictions on fence height, electric fencing voltage, surveillance camera placement, and data storage. Failing to comply can lead to fines or mandated removal of equipment.
Some industries face stricter demands due to the nature of their operations or the value of what their facilities protect:
- Energy and utilities: Sites in the energy and utilities sector like substations, power plants, and fuel storage yards must meet the physical security requirements of the Critical Infrastructure Protection (CIP) standard CIP-014-3. It states that perimeter security should include physical barriers, intrusion detection, access logging, and real-time monitoring.
- Transportation and logistics: Warehouses, freight yards, and shipping hubs in the transportation and logistics industry follow perimeter security guidelines from the Customs-Trade Partnership Against Terrorism (C-TPAT). Requirements include fencing, controlled entry, surveillance, and tamper-proof locks.
- Construction sites: Requirements for construction sites are less regulated, but insurers want to see that you are taking steps to secure your perimeter. Portable electric fencing, cameras, and lighting help reduce external theft and can lower premiums as a result. Local ordinances may restrict fence types or camera placement.
- Data centers: Facilities that store critical data need multi-layered security. Data centers follow System and Organization Controls (SOC 2) standards and must implement additional layers of perimeter security.
Implement an Integrated Security Plan With AMAROK
Investing in a single solution simply isn’t enough. An integrated approach ensures your facility accounts for the five D’s of security. Each layer helps transform your perimeter from an easy target into an effective deterrent.
Partner with AMAROK for industry-leading perimeter security solutions. It all starts with The Electric Guard Dog™ Fence, which has been tested by federally approved laboratories and meets American and international safety standards. Plus, our government relations and compliance team handles all permitting for your site to keep your perimeter security compliant.
To assess your site security needs, start with a threat assessment conducted by the AMAROK team. Our experts will identify potential vulnerabilities, including analyzing local crime data, and recommend a proactive solution for your unique commercial property. You can also download the PDF to learn more about securing your business.





