Property crimes accounted for 84% of all crimes in 2023, resulting in $280.5 billion in losses. As criminal tactics evolve and threats become more sophisticated, physical security is critical for protecting assets, people, and operations.
What is Physical Security?
Physical security refers to all protection measures that organizations implement to safeguard their assets, operations, and people from unauthorized access, damage, and theft. It’s the first defense against external threats and the foundation of any security strategy.
Effective physical security systems operate based on five fundamental principles, which we call the “Five D’s of Physical Security”:
- Deterrence: Measures that discourage potential threats through visible security elements.
- Detection: Systems that identify and alert security personnel to potential breaches.
- Denial: Elements that prevent unauthorized access through access control systems and credentialing.
- Delay: Mechanisms that slow down intruders, providing response teams time to intercept threats.
- Defense: Security personnel response, emergency procedures, and coordination with law enforcement.
These principles are implemented through a defense-in-depth strategy. This strategy involves multiple security layers working together to protect assets. This approach ensures that if one security measure fails, others remain in place to maintain protection. These layers include:
- The Outer Perimeter: It encompasses the property line and features measures like electric security fencing and video surveillance systems.
- The Inner Perimeter: Protects the exterior with access control points and intrusion detection systems.
- Interior Security: Protects specific areas within buildings.
- Point Protection: Safeguards individual high-value assets.
Components of Physical Security

Comprehensive physical security planning involves several parts that work together to create a robust security infrastructure, including:
- Perimeter security: The first barrier against intrusion is a property’s boundaries. Perimeter security measures, such as electric security fencing, serve as warning signs. Strategic security lighting complements these systems, eliminating shadows and dark areas.
- Access control: Gate Access Control systems regulate who can enter and exit a facility. They can range from lock-and-key setups to biometric scanners, multi-factor authentication.
- Video surveillance: Video surveillance systems, such as CCTV cameras, provide real-time monitoring and recording. These systems offer advanced features like motion detection, facial recognition, and remote viewing capabilities.
- Intrusion detection: Building intrusion detection systems alert security personnel when unauthorized entry occurs. These systems can include door and window sensors, glass break detectors, and motion sensors.
- Visitor management: Visitor management systems control and track the access of visitors to a facility. This can include check-in procedures, visitor badges, and escort requirements.
- Emergency response: Effective physical security planning must include emergency response. Emergency response systems often include mass notification capabilities and automated protocols that can lock down specific areas or entire facilities as needed.
Why Companies Need to Focus on Physical Security

Organizations must prioritize physical security planning as a fundamental business function, rather than viewing it as an overhead expense. As threats continue to evolve, sweeping security solutions provide a significant return on investment (ROI). Investing in physical security offers numerous benefits, including:
1. Asset Protection and Loss Prevention
Cargo theft incidents across the United States and Canada increased by 14% in Q3 2024 compared to Q3 2023. Effective physical security management prevents external theft, vandalism, and unauthorized access through integrated deterrence and detection measures.
Property crimes often target businesses during non-operational hours, making after-hours security critical. Physical security solutions can reduce shrinkage rates and protect valuable assets from theft or damage. You can also safeguard essential infrastructure, intellectual property, and sensitive data storage locations from physical breach attempts.
2. Regulatory Compliance
Strong physical security measures help organizations address multiple regulatory requirements simultaneously. Many industries face specific security mandates, such as:
- North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP)
- PCI Security Standards Council (PCI SSC)
- Customs Trade Partnership Against Terrorism (C-TPAT)
Comprehensive security systems provide the necessary controls and documentation to demonstrate compliance during audits and inspections, helping avoid costly fines and penalties.
3. Operational Continuity
Security breaches can disrupt business operations, leading to lost productivity and revenue. Physical security systems support business continuity by preventing these disruptions before they occur. If incidents do happen, integrated security solutions enable rapid response and recovery.
Additionally, automated security systems streamline access management, visitor processing, and monitoring functions. Improve operational efficiency and reduce manual security procedures with an automated security system.
4. Reputation Protection
Security incidents can quickly become public relations challenges. Companies that experience repeated theft or security breaches face damaged customer confidence and negative media attention.
Implementing robust physical security systems demonstrates a commitment to protecting customer assets and information. This commitment builds trust with stakeholders and differentiates you from competitors.
5. Workplace Safety Enhancement
Comprehensive physical security measures contribute to employee safety and well-being. Employee morale while on the job tends to increase when workers know their safety is being protected.
6. Cost Reduction
Proper security measures provide substantial financial returns through multiple channels. Insurance providers often offer premium reductions for businesses with security systems. In addition, security solutions and any associated monthly subscription fees are typically tax-deductible as operating expenses.
7. Legal Liability Protection
Physical security helps protect organizations from premises liability claims by demonstrating due diligence in protecting visitors and occupants. Clear documentation of security measures, regular system testing, and incident response procedures can provide vital evidence in legal proceedings.
Best Practices for Ensuring Physical Security
Adequate protection requires following security management guidelines. The following best practices are standards for developing, maintaining, and optimizing security programs:
Conduct Comprehensive Security Assessments
A thorough physical security audit is the first step to ensuring effective security measures. Analyze location-specific risks, historical incident patterns, and emerging threats that could impact your facility.
Document vulnerabilities across your entire operation, from perimeter access points to areas inside your buildings. Consider obvious risks and subtle weaknesses that criminals could exploit. Use this assessment to establish security objectives and create an implementation roadmap.
Implement Layered Security Systems
Design your security infrastructure using the defense-in-depth principle. Start at your property line with robust perimeter security measures like electric fencing and intrusion detection systems. Add intermediate layers of protection through building access control and video surveillance.
Establish additional security controls around specific high-value assets or sensitive areas. Ensure each layer operates independently while working together with other protective measures.
Establish Access Control Protocols
For optimal physical security management, the principle of least privilege should govern your access control strategy. Define access levels based on job functions and regularly audit these permissions.
Create clear procedures for managing temporary access, visitor entry, and contractor oversight. You should also deploy multi-factor authentication for sensitive areas and maintain detailed access logs. Review these logs routinely to identify suspicious patterns or unauthorized access attempts.
Deploy Strategic Surveillance Systems
Position video surveillance equipment to eliminate blind spots and optimize coverage of critical areas. Use video analytics to flag suspicious activities automatically. You should also create straightforward policies for footage retention and review.
Train personnel in surveillance procedures and incident response protocols. Regularly test camera systems and maintain backup recording capabilities for critical areas to ensure continuous monitoring.
Develop Emergency Response Procedures
Proper emergency response procedures can protect staff and customers during a security breach and ensure minimal property damage. Create detailed response plans for various security scenarios, from minor breaches to major incidents.
Train Security Personnel and Staff
Human error is one of the most significant security risks for organizations. To counter this, develop comprehensive training programs that cover all aspects of your security operations. These programs should include technical training on systems and general security awareness education.
Track and Protect Critical Assets
Thieves prefer portable and high-value items, so protecting these assets is a crucial part of physical security. Establish special protection measures for high-value items. A key step is to integrate asset management systems with your security infrastructure.
Implement a tracking system for valuable equipment and maintain real-time location data. You should also have procedures for asset movement and maintain detailed chain of custody records. Conduct regular audits to verify asset location and status.
FAQs
Here are answers to commonly asked questions about physical security best practices.
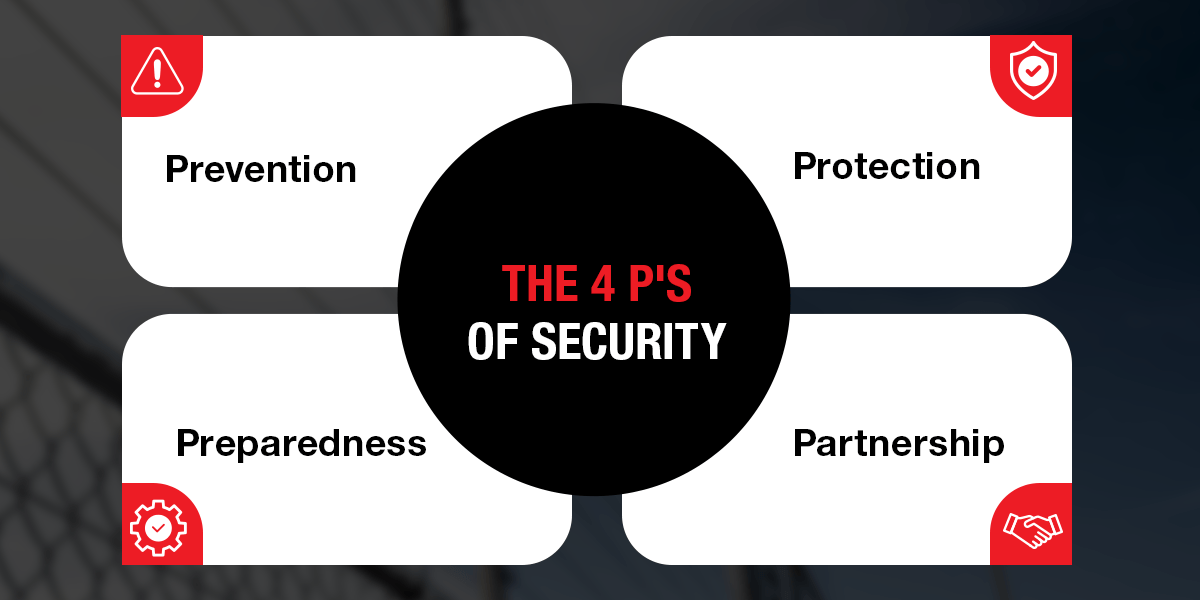
What Are the 4 P’s of Security?
The four 4 P’s of security form an extensive framework for security planning:
- Prevention focuses on stopping incidents before they occur.
- Protection involves safeguarding assets and people.
- Preparedness ensures readiness for potential incidents.
- Partnership emphasizes collaboration with law enforcement, emergency services, and other stakeholders to enhance security effectiveness.
How Often Should Physical Security Audits Be Conducted?
Organizations should conduct comprehensive physical security audits at least annually, with additional focused assessments following significant operational changes, security incidents, or facility modifications. Monthly or quarterly informal assessments can help you identify emerging vulnerabilities. Industries with specific regulatory requirements may need more frequent audits to maintain compliance.
What’s the Difference Between Security Risk Assessment and Vulnerability Assessment?
A security risk assessment evaluates potential threats, their likelihood, and their potential impact on operations. It considers internal and external factors affecting security.
A vulnerability assessment identifies weaknesses in existing security measures that criminals could exploit. Together, they provide a complete picture of security needs and priorities.
Heighten Your Physical Security With AMAROK’s Multi-Layered Solutions
Protecting your assets requires a comprehensive, layered approach to physical security. AMAROK delivers the ultimate perimeter security solutions, including The Electric Guard Dog™ Fence, integrated video surveillance, Gate Access Control, and building intrusion detection. We are proud to secure over 8,000 sites, and the average AMAROK customer saves $120,000 annually when they replace 24/7 security guards with our system.
Contact us today or request a threat assessment to see how our solutions can help secure your business or facility against external theft.






